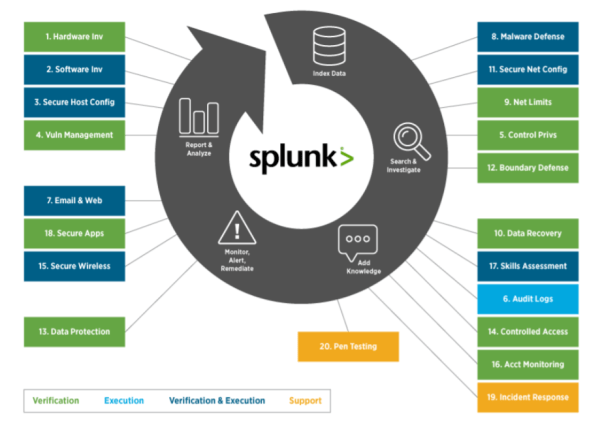
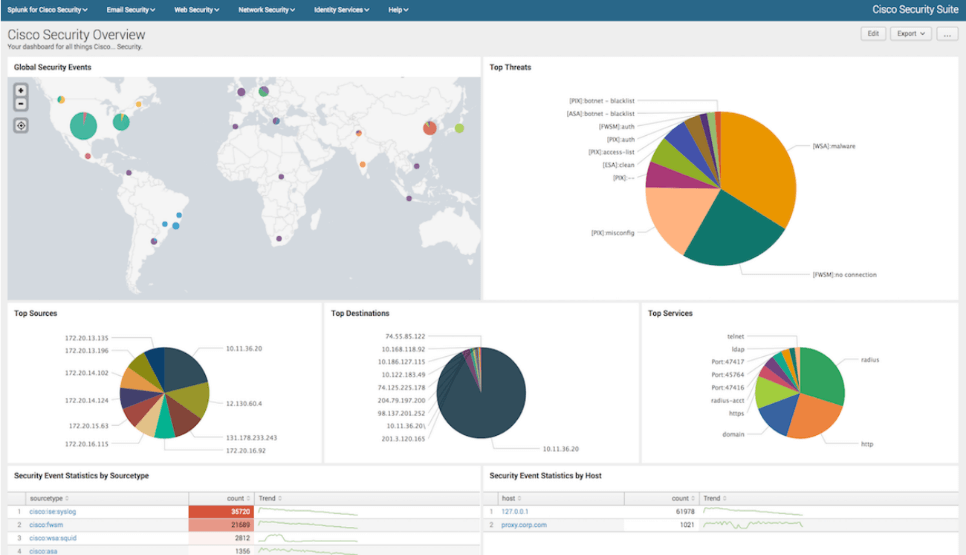
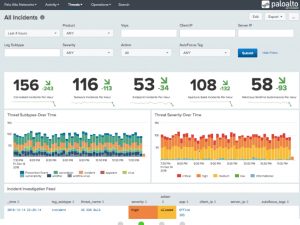
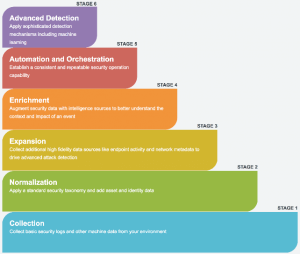
Many people consider Splunk a point solution and it is often forced into many categories – Log aggregator, SIEM, Big Data analytics, data store, etc. The truth of the matter is, Splunk can (and does) fit into all of these categories. Splunk is a platform that excels in ITOPS, Security, Data Analytics, and many other areas. But for the sake of this article, we are going to be focusing on how Splunk (and Splunk Enterprise Security) can bolster your security posture as an organization.
Security with Core Splunk
A top-down approach to securing an organization is ideal. It starts with directive security – policies and procedures – followed by a preventive, detective, and corrective controls. But what many people don’t consider when implementing security controls are the man-hours involved in analyzing these security events, and administering/maintaining these tools.
This is where core Splunk comes in. It provides you with organizational visibility by combining all of your security controls into one single pane of glass. Core Splunk (the base Splunk product) is ideal when it comes to aggregating these logs from virtually any device or tool in your network.
What Splunk does better than almost anybody is being so universally accepted to the method in which it receives data. Whether it is Windows Events from servers and endpoints, syslogs from network devices such as routers, switches, or firewalls, API calls from cloud applications such as AWS, GSuite, or Okta, Splunk can accept it, and accept it rather easily.
Once your data is in, you can begin to transform, analyze and visualize your data. Splunkbase has almost 3,000 applications dedicated to helping you through this process, and over one-third of these are specific to security controls. You will find some of the bigger names in the security space there, from Cisco to Palo Alto, Nessus, McAfee, Qualys, Rapid 7, and everything in between.
But What About Use Cases?
I know, Metrics are great, but learning how to traverse the raw data and look for threats, that’s where the fun is! Splunk knows this and has gone to great lengths to help you go from an organization that just collects logs, to an organization actively thwarting bad guys. Here’s how.
Splunk has built several FREE applications dedicated to helping you become more proactive instead of reactive when it comes to securing your environment. Some of these apps that we will talk about are essential:
- Splunk Security Essentials
- Splunk Security Essentials for Ransomware
- Splunk Security Essentials for Fraud Detection
- Splunk Essentials for ICS Security and Compliance
- Splunk Essentials for the Financial Services Industry
Splunk Security Essentials
For the sake of time, we will only focus on the original – Splunk Security Essentials. But feel free to take a look at the whole suite of Splunk essential apps!
What the Splunk Security Essentials app will do for you is provide you with over 125 common (and some not so common) security use cases.
Not only does it provide you with the SPL (search processing language) search string, but it also utilizes sample data to show you what the results will look like if you have matches in your environment relevant to the particular use case.
My personal favorite feature is the data check. The Security Essentials app will actually search through your data and tell you if you have ingested the right data sources to satisfy each use case.
This is great because it provides you with a simple path to help you mature not only your Splunk environment but also your security posture as an organization because it will help you identify gaps in your network security that you may not be aware of!
Security Maturation with Splunk Premium Apps
If you aren’t aware, Splunk also offers some premium applications (Enterprise Security and User Behavior Analytics) that are a separate paid license that helps bolster your security posture. Security Essentials identifies use cases that some of these premium apps may satisfy and it clearly identifies them which will help you get an idea of what those apps may offer.
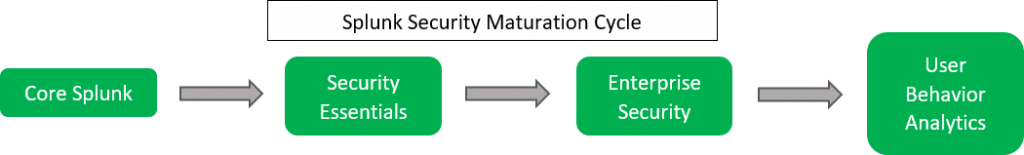
The next step in what we like to call “The Splunk Security Maturation” cycle would be these premium apps. Splunk Enterprise Security (ES) and User Behavior Analytics (UBA). Splunk Enterprise Security has become a staple across the SIEM world and can be found in Gartner’s report in the Leaders quadrant for the highest overall “Ability to Execute.”
Splunk ES takes security to the next level with your logs by not only correlating data but also using machine learning to make alerting contextual instead of setting static thresholds. These contextual alerts are one of my favorite aspects of ES because not only is each environment different, but no environment is stagnant. They are always changing. So, a particular static threshold may work for your organization this month, but it won’t next month. These contextual searches baseline your environment and they adapt and change with what is happening across your organization. If you haven’t already, head over to our post here to see what ES is all about!
What I cannot stress enough about our cycle mentioned above, is that you cannot skip through the process. A solid core Splunk infrastructure is essential to make any of this work and trying to rush through the maturation process will leave you with a halfway working shelf ware product long before you will ever fully reap the benefits.
So, to wrap it all up, Splunk is not inherently a security product, but it is a platform that does security extremely well! You do not need to purchase premium applications to be able to move your core Splunk infrastructure towards a security solution. ROI on security is tough. Many organizations do not take security seriously until it is too late. Splunk is here to help you develop your use cases and show your leadership that security is no longer a commodity, but a requirement. And as always, do not hesitate to reach out to Aditum Professional Services if you need help with bolstering your security posture, or navigating through the Splunk Security Maturation Cycle.
SP6 Can Help You Improve Security with Splunk
SP6 is a Splunk consulting firm focused on Splunk professional services including Splunk deployment, ongoing Splunk administration, and Splunk development. SP6 has a separate division that also offers Splunk recruitment and the placement of Splunk professionals into direct-hire (FTE) roles for those companies that may require assistance with acquiring their own full-time staff, given the challenge that currently exists in the market today.